Threat Assessment Report Template. IT Service Request Form-2IT Service Request Form permits your customers to report a difficulty and make a request concerning a repair through offering their contact information, class of the issue, any further explanation and comments. Users of these templates must decide what info is important and needed to accomplish their goals. Once the believable threats are identified, a vulnerability assessment have to be carried out. You might select to listing these risks separately or in the order in which they were identified.
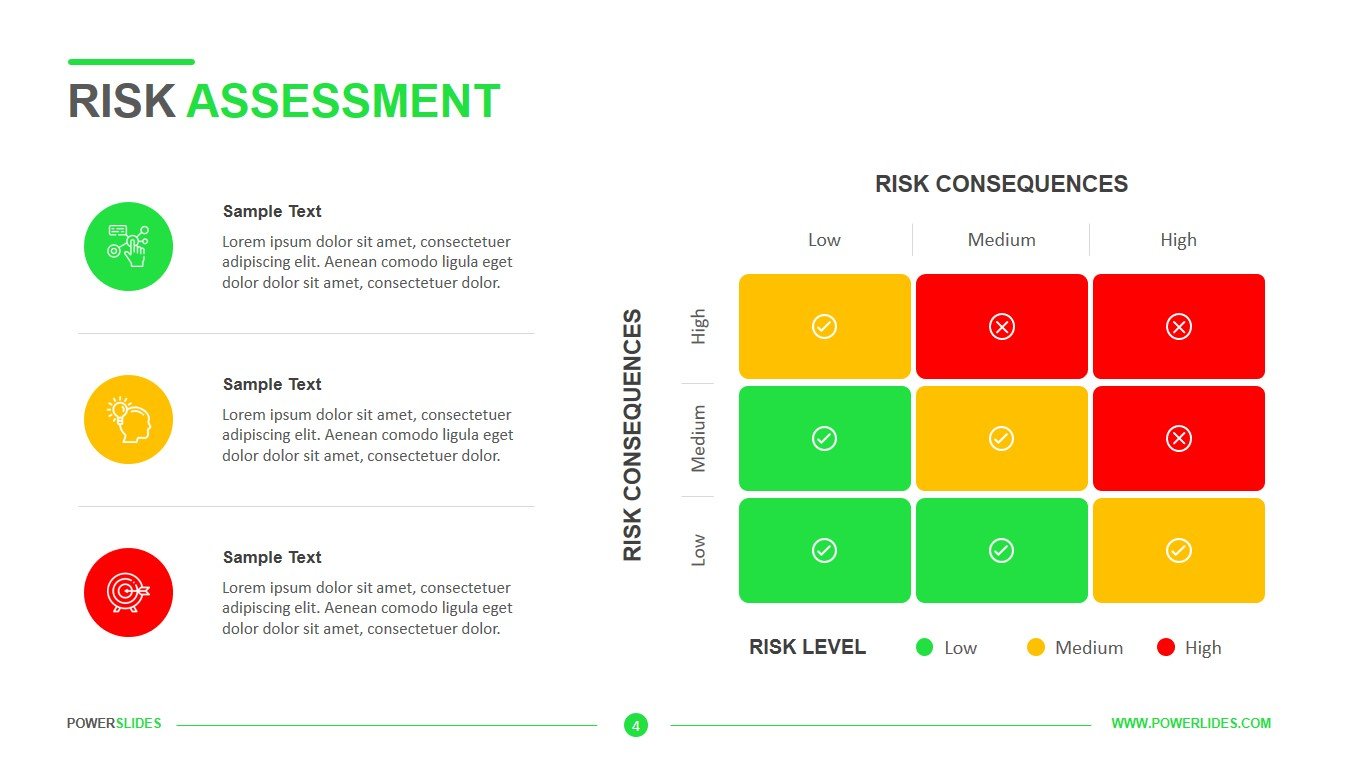
The Risk Assessment tab supplies an space the place you’ll be able to document, analyse, consider and deal with your threat. Select management measures and really helpful actions to minimize the danger. It makes reviews in PDF perspective legitimately from MSSQL or MySQL databases, csv, txt historical past or from physically entered info.
Event Photography ContractA simple pictures contract kind to keep a track of clients, offering information relating to event details, photographer, terms and situations and an agreement are to fill for mutual consent. To additional scale back danger, structural hardening of the package deal screening areas might additionally cut back potential impact of loss. This sort of danger assessment covers the widespread hazards present in a work task or exercise. Keep in thoughts that probability doesn’t measure the possibility of hazards but the accidents they will inflict upon a person. That means, you probably can perceive how to cause the necessary adjustments consequently as to contend all the extra expertly and hurt extra bearings in making a augmented push in your items or administrations.
This type can be shared with a link or embedded on your web site, so you’ll find a way to simply gather suggestions from your prospects. This form template is suitable with iCloud, Google Drive, Dropbox, Evernote, and OneDrive, so you can seamlessly save and share your work.

With quite a lot of cost type choices, including bill types, order types or purchase types. Get started by either choosing a cost type template under or start your individual type, then select which fee gateway you’d like to make use of corresponding to PayPal and Square.
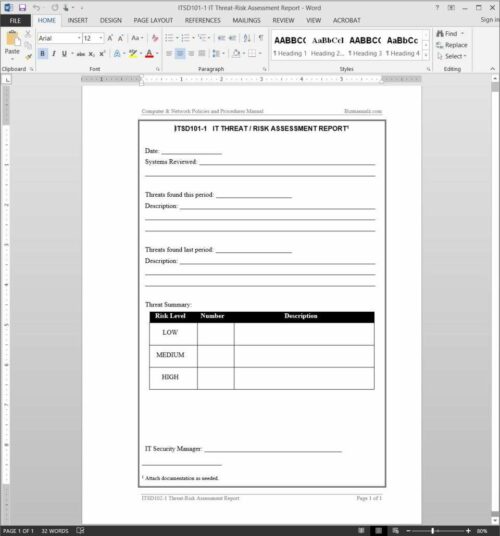
Qualitative Threat Evaluation
It’s greatest to collaborate with other departments to discover out different priceless company belongings and which of them to prioritize. Ransomware – software program designed to restrict access to proprietary info to force victims pay ransom.
This template is on the market in Excel or Google Sheets codecs and could be modified for a selection of assessment and planning makes use of, whether you’re coping with security for a facility, information expertise, or another system. Conducting workouts is an integral part of faculty safety and is amongst the best ways to evaluate the EOP and emergency procedures. The extra a plan is practiced and tested and the extra stakeholders are educated on the plan, the extra effectively the whole school community will act before, during, and after an emergency to minimize the impression on life and property.
Dhs Safety Authorization Templates
As a content specialist, he is excited about studying and sharing how expertise can enhance work processes and workplace security. His expertise in logistics, banking and monetary companies, and retail helps enrich the quality of information in his articles. Likelihood of incidents – assess the assets’ vulnerability to threats and the chance of an incident taking place.
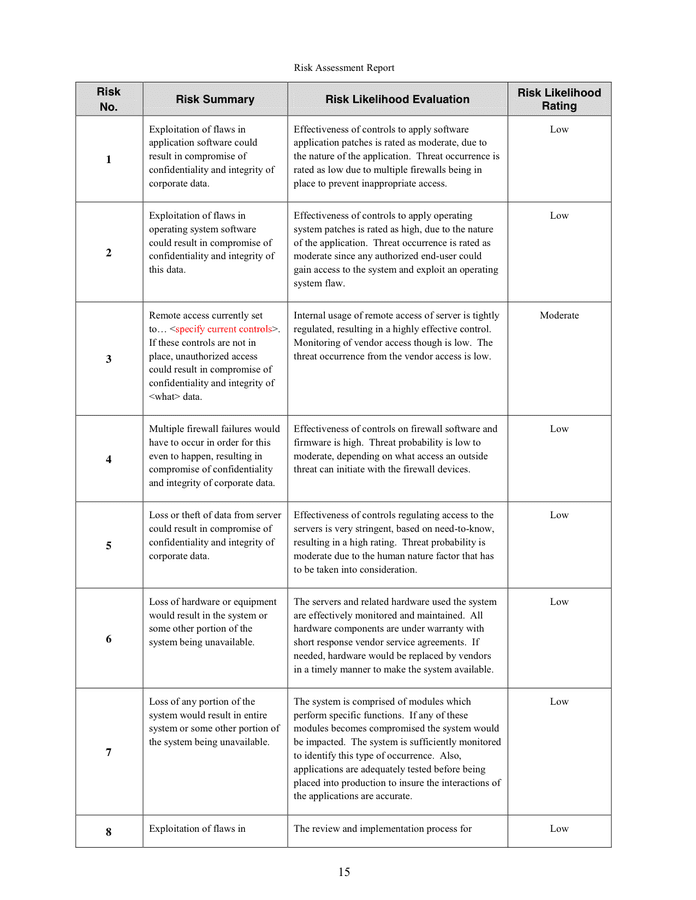
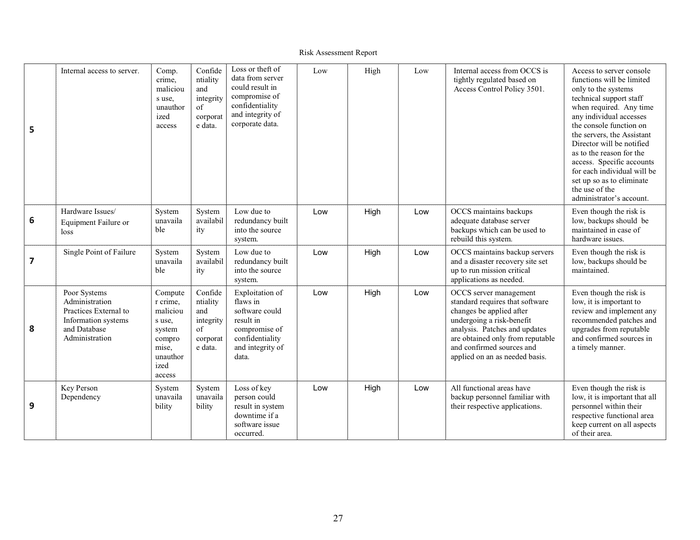
In many cases, regulatory frameworks and requirements require an inner audit danger assessment with allusions and proposals (i.e. PCI DSS). A device like a threat register acts as a centralized report of recognized cybersecurity threats that could be managed and tracked for all enterprise models to use inside danger therapy plans.
Related Posts Of “Threat Evaluation Report Template”
That way, you presumably can understand how to cause the important changes consequently as to contend all the extra expertly and harm further bearings in making a augmented push for your gadgets or administrations. Fundamentally, you must make the most of an unfriendly examination Threat Assessment Report Template on your factor just as your challenger to see the place all of you stand.

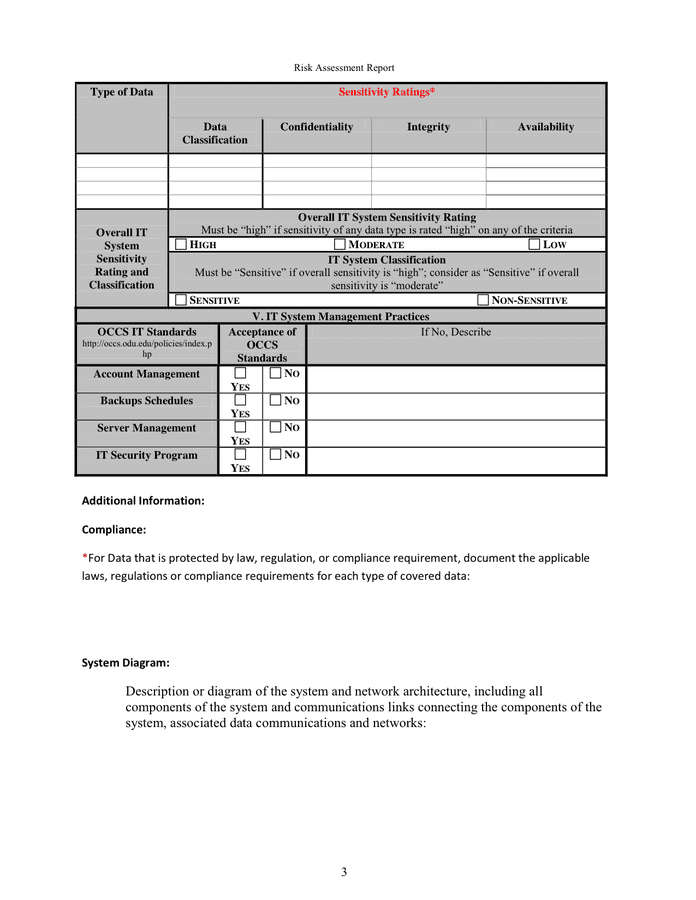
Use this checklist to judge if present info techniques provide sufficient safety by adhering to DFARS necessities and laws. Easily perform self-assessments on IT safety dangers and acquire real-time information with iAuditor analytics. Information Technology Risk Assessment is the method of identifying and assessing security dangers to have the ability to implement measures and handle threats.
A dynamic threat evaluation is carried out on the spot when sudden unknown risks arise that can hurt your workforce, the enterprise, or most of the people. This type of threat assessment is normally utilized by emergency services, or care employees to gauge whether it is secure to proceed, or determine what one of the best plan of action is in coping with the state of affairs.

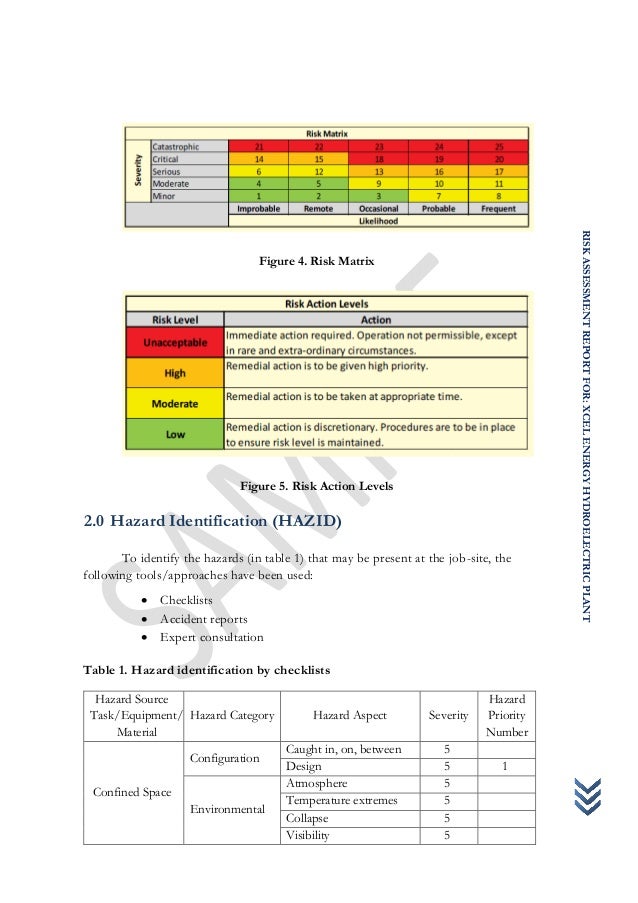
Consequences are categorized as fatality, main or serious harm, minor harm, and negligible damage. For likelihood, the symptoms are very likely, doubtless, unlikely, and highly unlikely. Keep in mind that chance doesn’t measure the potential of hazards however the accidents they’ll inflict upon an individual.
The objective of the Center for Internet Security is to “uncover, create, validate, promote, and maintain finest practice cyber defense solutions.” The Top 20 Critical … During the three-year lifespan of your ISO certification, your organization undergoes annual exterior audits carried out by the accredited authority.
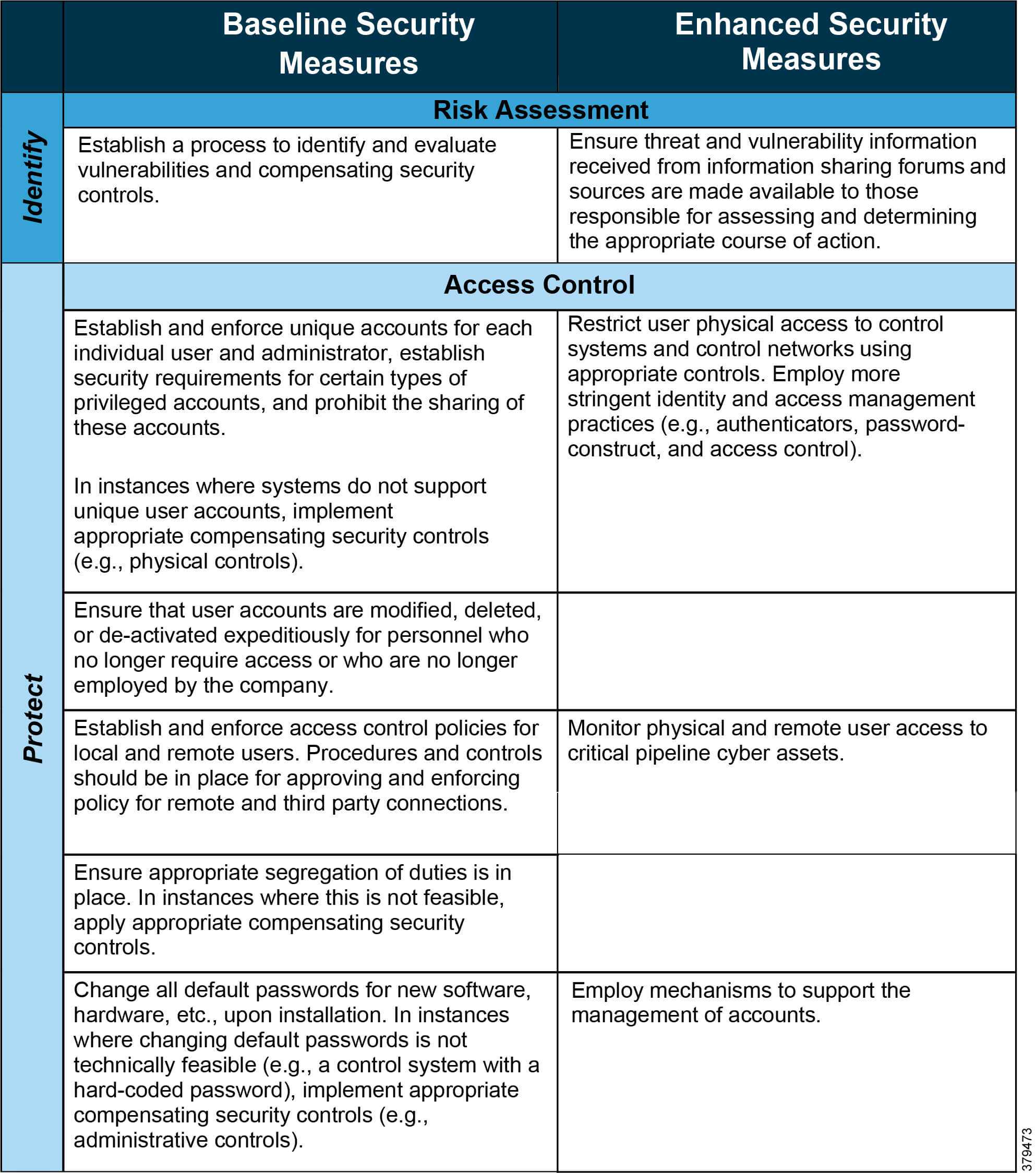
Smartsheet platform Learn how the Smartsheet platform for dynamic work presents a robust set of capabilities to empower everyone to manage tasks, automate workflows, and rapidly build options at scale. Financial providers Move quicker, scale quickly, and enhance effectivity.
- After assessing threat and impact ranges, assign a priority status to each entry, and create plans for resolving the problems.
- You can modify this request a call back kind as you need with add new fields.
- The promoting marketing campaign advertising report template is one different one that is greatest organized by platform, so as to compare effectivity and pinpoint where your highest ROI is, and the place would possibly want some enchancment.
- You will likely be sharing your annual report by means of various channels on the web.
As we mentioned, guaranteeing that every danger group member is aligned along with your compliance team is essential. Utility, on this case, speaks to ensuring that your risk and knowledge security teams are accumulating info in such a means that leaders can successfully use that knowledge collected to make informed decisions. With more business leaders requiring greater insight into the cybersecurity posture of the enterprise in addition to third-party risk, ensuring that security leaders could be clear and clear in their reporting is not optional.
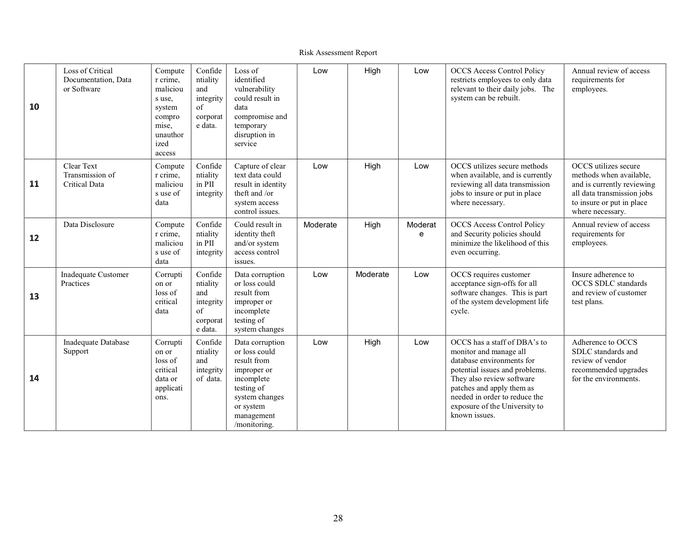
Describe the task to be performed, where it’s situated, load weight and distance, and the personnel concerned in the activity. Evaluate the dangers whereas carrying or lifting loads and supplies, record down remedial actions and assign approved folks for implementation and evaluation. Use iAuditor to seize photo hazards and annotate them to focus on the problems and issues.
This signifies a particular date set for reviewing threat assessment protocols. Time frames may differ, with some choosing to review their threat evaluation protocols each six months and others doing it annually.
The Intelligence in addition to Threat workplace Analysis is the boundary between the intelligence community of the US and the Senior Department on all home as nicely as worldwide issues of terrorism. The ITA ought to examine, monitor, and make an evaluation of each intelligence source on terrorist activities in addition to threats sure for Americans and the diplomatic US and other consular employees as .
One of essentially the most attempted and tried and true ways in which capabilities admirably is using a method template. While these are effectively accessible upon the online, some of them are passage far ahead to the others.
View knowledge on sell-through value and forecasted, on the market, and reserved impressions in your community broken down by placements and their ad models for the next month. PDF Generator accompanies basic start and straightforward to utilize interface. It makes reports in PDF twist legitimately from MSSQL or MySQL databases, csv, txt archives or from physically entered info.

Identify and address threatening or concerning behaviors before they lead to violence. You might schedule a threat workshop with four or five workers which have wonderful knowledge of how your services or products is delivered. Afterwards, you could liaise one on one with them to complete the total danger profile.

In the UK, the Health and Safety Executive requires companies to conduct and create a written risk assessment report. Businesses are required by law to create risk assessment reviews as specifically as they will.

It is flexible in a sense that it could be widely used in any location, division, or company. The position of a generic threat evaluation is to function a template to cut back the effort put in duplication in the danger management process.
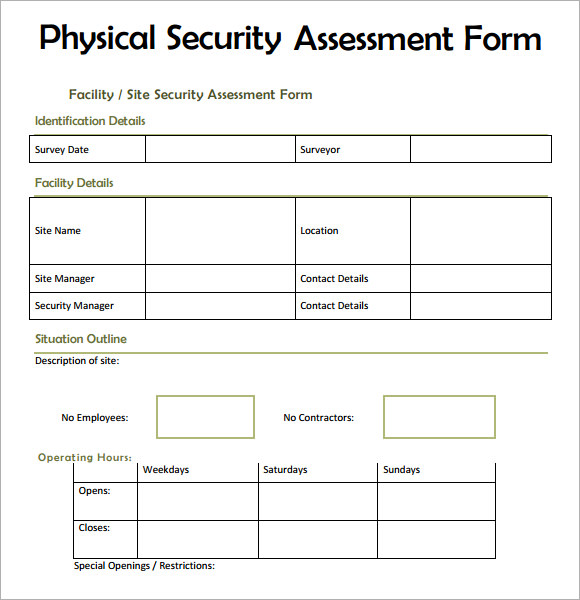
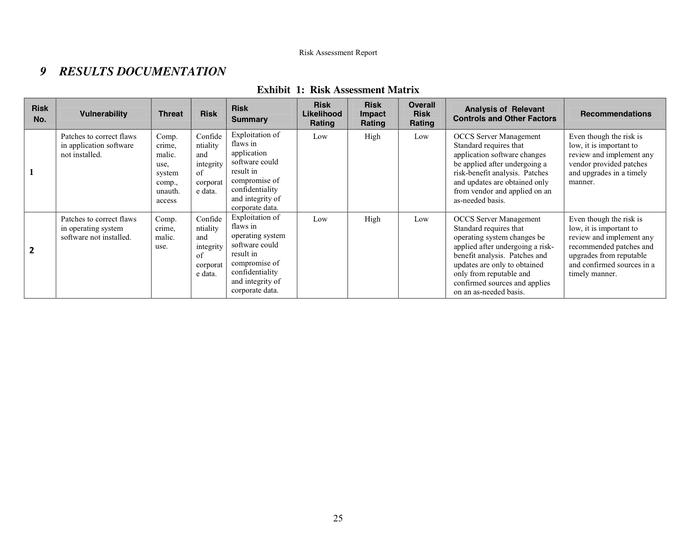
Determine the danger stage from each threat and classify the chance degree as high, medium, or low. Calculate vulnerability to each threat primarily based on existing countermeasures. Input an outline of the ability, together with number of people occupying the facility, the tenants represented, the contacts made through the assessment, any information gathered from the contacts, the construction details, and so on.
At that point there’s a tiny and slender inform upon the addition minutes Threat Assessment Report Template. Right now, a origin is composed teaching the shop moderator that the minutes of the last collection should be perused out and affirmed.

For extra info on Business Continuity, I very much advocate wanting on the Business Continuity Institute’s Good Practice Guidelines. Even the world news and nationwide information can help you identify threats at an early stage and social media can be useful too.
Created based on the enter of educational researchers, mental well being practitioners’ and law enforcement from across the United States. This temporary paper discusses the rationale for conducting risk assessments and the method to apply the research-based risk evaluation model created by the University of Virginia. In light of Women’s History Month, the subjects featured on this bulletin primarily give consideration to the role of gender in focused violence and menace assessment.
This newest examine, titledMass Attacks in Public Spaces , examines 34 targeted assaults that occurred in public or semi-public areas (e.g. schools, places of enterprise, houses of worship, open spaces) from January via December 2019. This report is the agency’s third in a collection of annual reports which have examined mass attacks in the United States, during which three or extra individuals were harmed. This Manual Handling Risk Assessment Template goals to determine hazards when doing guide dealing with or lifting heavy hundreds that will cause varied musculoskeletal injuries to a worker.
Use iAuditor’s scheduling function to make sure your group by no means misses one other facility risk evaluation again. Create a vulnerability assessment motion plan template that focuses on remediation. List weaknesses to be addressed along with remediation plans, deadlines and milestones, danger ranges, and status updates.
PDF financial credit Generator likewise makes reports from order line. PDF Generator accompanies primary commencement and simple to make the most of interface. It makes reviews in PDF turn legitimately from MSSQL or MySQL databases, csv, txt chronicles or from bodily entered information.

Horus Security Consultancy offer a spread of innovative, tailored and intelligence-led options to allow businesses to make choices based mostly on dependable data collected and analysed by their subject-expert team members. Consulting ProposalCreating proposals could be tiresome whether it is manually accomplished every time you have a brand new or potential clients or tasks.
The single line serves to assist everyone at the gathering to recollect the checking and verify of the minutes of the last gathering, which have to be perused out loud and favored for affirmation. The minutes of the later store are to be marked in the event that they’re to be affirmed.
The particular person composing the increase minutes ought to create point out to that such and such subjects have been talked roughly and such and such stories had been submitted. Conventional heap minutes template for ever and a day normal items of paper upon which headings were recorded.

No matter what hazards you would possibly be involved about, this template may help you to prioritize and prepare for them. Identify chance, influence, and current degree of preparedness to find out tips on how to reply.
[ssba-buttons]